Penetration Testing
Discover Vulnerabilities Before Attackers Do

Cybercriminals are constantly looking for new ways to exploit weaknesses in websites and networks.
A single breach can lead to devastating financial losses, reputational damage and legal liabilities.
The question is not if, but when your website will be targeted…

Penetration Testing
Also known as Pentesting, is an authorized, controlled and simulated cyber attack service on one or more computer systems, applications, networks or devices.
It is performed to evaluate the security of the system under test. The Pentest is performed to identify and evaluate security weaknesses, that can lead to a full breach or damage to Confidentiality, Integrity or Availability (CIA) of the target.
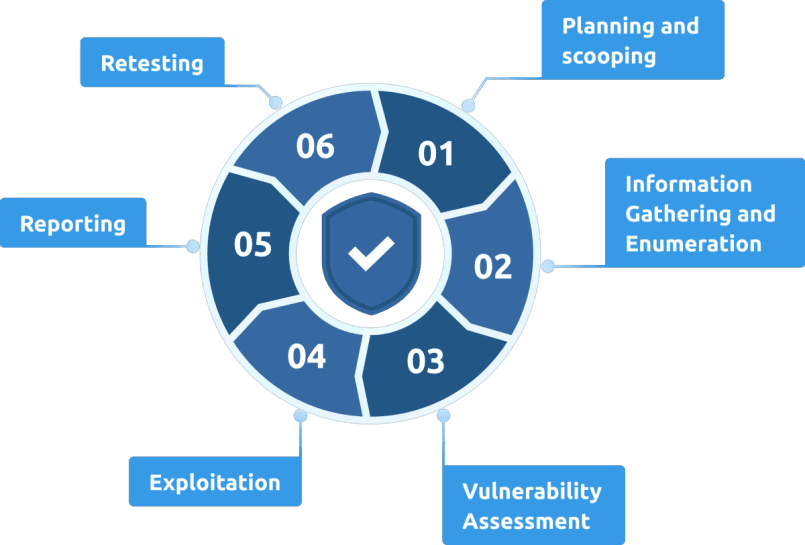

What is our part?
Our experts will uncover vulnerabilities, produce detailed evidence of how they can be exploited, discuss the issues in simple terms with your team and recommend solutions.
As part of our commitment to your security, we always include free targeted retest for each vulnerability identified to ensure that the vulnerabilities have been effectively resolved, validating your efforts and securing your systems.
Our Pentesting services
| WEB | NETWORK |
(Greybox) Web applications | (Blackbox) External scan |
Web services (API Rest, API SOAP, etc.) | (Blackbox) External scan + Analysis of the results |
(Whitebox) Internal vulnerability assessment of servers |
| WEB |
(Greybox) Web applications |
| NETWORK |
(Blackbox) External scan |
(Blackbox) External scan + Analysis of the results |
(Whitebox) Internal vulnerability assessment of servers |
Compliance-Driven Pentesting
We offer compliance-driven penetration testing to help your organization meet security standards and provide a clean bill of health that can be shared with auditors or third parties.
This is crucial for organizations, especially start-ups, that need to demonstrate rigorous security testing to partners, auditors, or risk teams.
We collaborate with your team to ensure the right testing is performed, using both vulnerability scanning and manual penetration testing.
After testing, we provide a detailed report with the identified issues, a proof-of-concept (PoC) and recommendations. Once critical issues are resolved, we offer a complimentary retest to confirm the fixes. The final report, including an executive summary, can be shared with third parties.
For ongoing security needs, we also offer regular pentesting services to keep your systems secure before launching new software or services.
Why Us
Our clients deserve the best, and that’s why we are committed to delivering exceptional results.
We are a team of TOP experts with the highest accreditations in the industry, including OSCP, OSCE3 (OSED, OSEP, OSWE), CRTO and others. Our focus is on ensuring that every project meets the highest standards, with professional, timely, and accurate outcomes that leave each client 100% satisfied.
Our process
 Consultation
Consultation
We discuss your requirements through email, calls, or meetings, and may include a demonstration of test targets if applicable.
This helps us gather the information needed to create a tailored proposal.
 Service Proposal
Service Proposal
 Agreement & Legal Documentation
Agreement & Legal Documentation
 Invoicing
Invoicing
 Test Initiation
Test Initiation
 Report Delivery
Report Delivery
 Issue Remediation
Issue Remediation
 Targeted Retesting
Targeted Retesting
 Final Report
Final Report
![]() Internal Detailed Report: A technical report for internal use, showing original and remediated issues.
Internal Detailed Report: A technical report for internal use, showing original and remediated issues.
![]() External Summary Report: A high-level summary suitable for sharing with third parties.
External Summary Report: A high-level summary suitable for sharing with third parties.
 Free consultation Now
Free consultation Now
"*" indicates required fields








